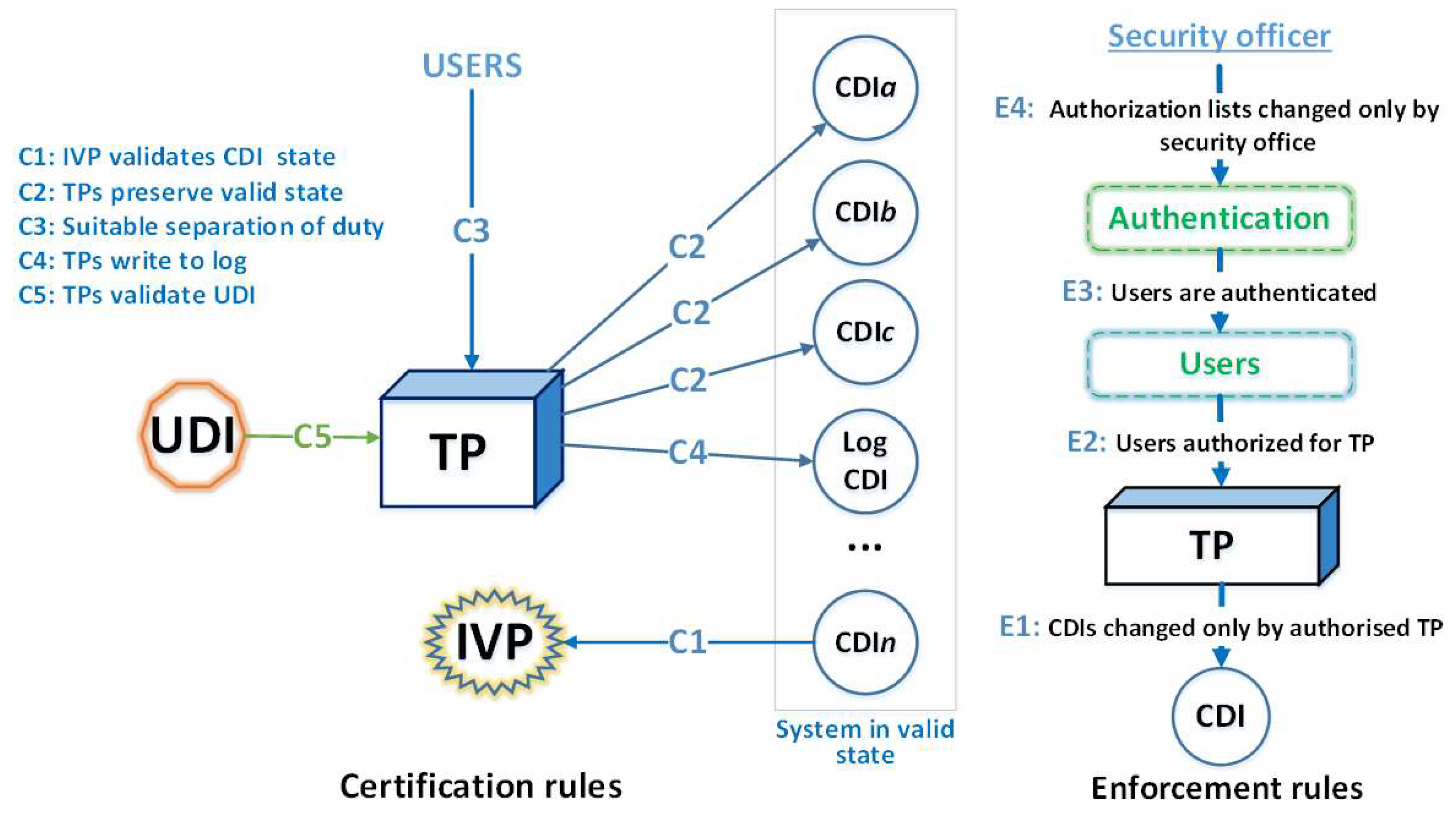
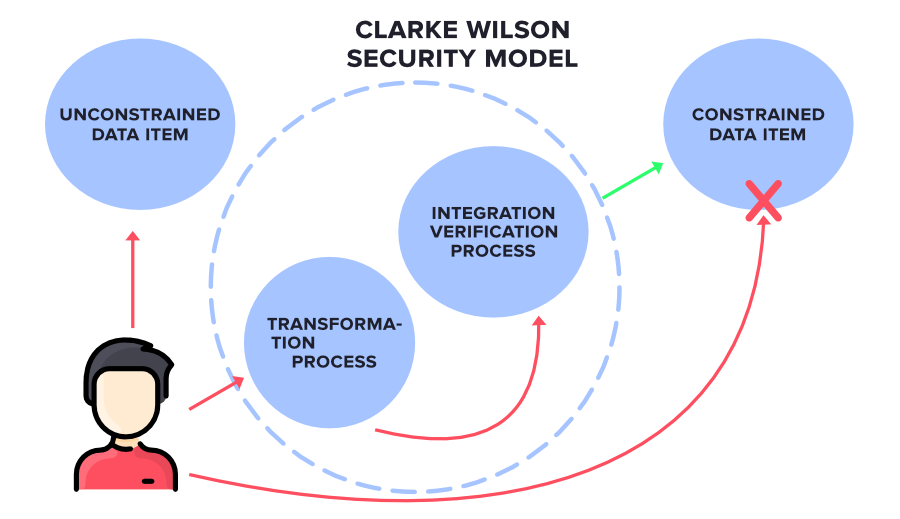
1 The relationship between different entities in Clark-Wilson Integrity... | Download Scientific Diagram

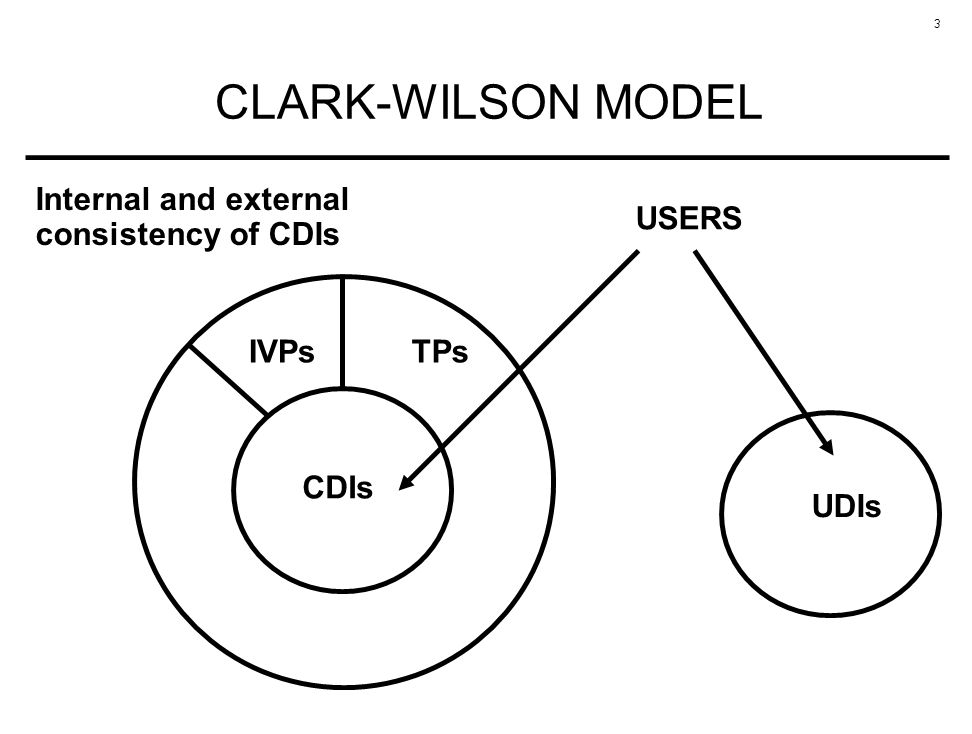
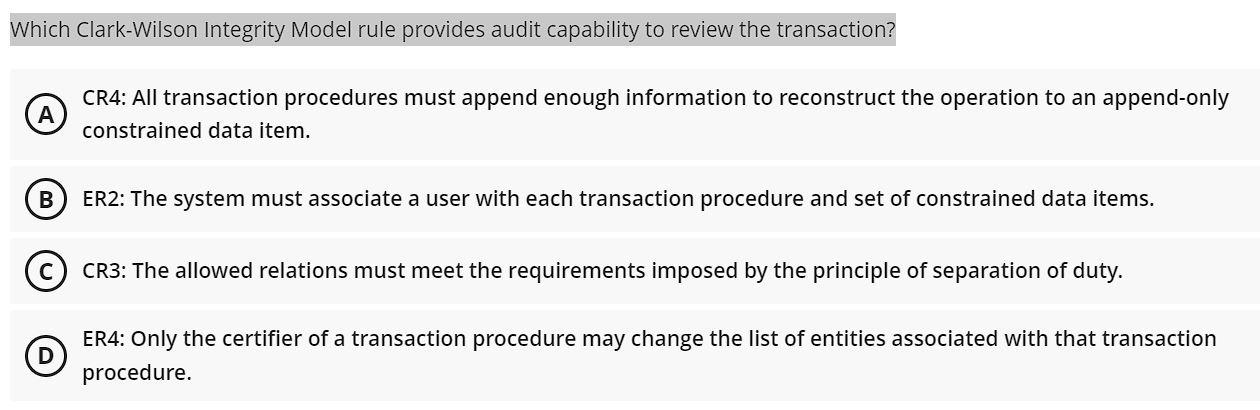
Clark- Wilson Model - CLARK-WILSON MODEL Integrity policy motivation ➢ In commercial environments, - Studocu

Clark-Wilson Model - Model Integrity policy: motivation In commercial environments, who examines and - Studocu
Evaluation of the Appropriateness of Trust Models to specify Defensive Computer Security Architectures for Physical Protection S
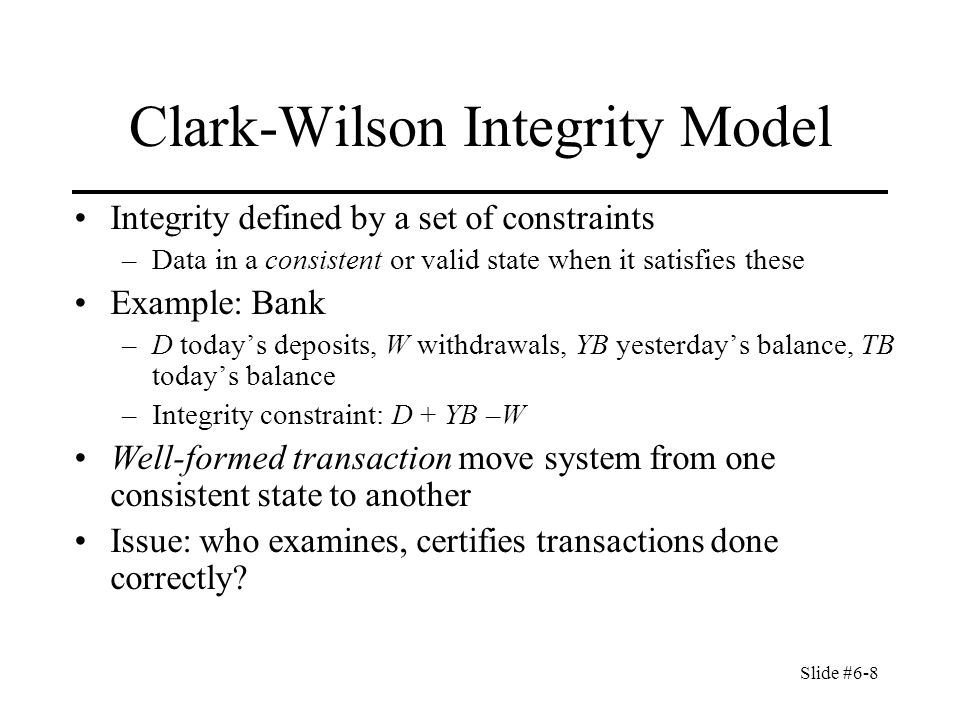
Slide #6-1 Chapter 6: Integrity Policies Overview Requirements Biba's models Clark-Wilson model. - ppt download